Managing Users and Roles with RBAC
Using Role Based Access Control (RBAC), you can configure access policies and manage users for your group—your organization.
All the procedures and discussions in this helpsite page assume that RBAC is already enabled for your organization. If it is not, contact Pepperdata Support.
On This Page
About Group Administrators
A Pepperdata group administrator is a Pepperdata dashboard user—someone who has a Pepperdata account already set up—who has privileges to configure access policies and to add and remove other Pepperdata dashboard users (Pepperdata accounts).
To obtain group administrator privileges, contact someone in your organization who already has group administrator privileges, and ask them to grant you access. If there is nobody in your organization with group administrator privileges, contact Pepperdata Support.
As a group administrator, whenever you use the Pepperdata dashboard to make changes to users’ access permissions or to access policies, the changes take effect immediately because policy permissions are evaluated for every request. For example, if you change the access policy for a user while they are logged in to the Pepperdata dashboard, they will see the effect the very next time they refresh their browser page or navigate to a different page.
Add a Pepperdata User Account
When you add a user, you configure which users and queues they can access. If you restrict their access to resources in any way, the user will be will be unable to access reports or to perform dashboard configuration, and will be able to see only dashboard pages that are specific to their accessible resources (as specifically configured in an access policy, or a resource that you did not restrict). Conversely, you can grant group administrator privileges to a user, to allow them to see everything, configure access policies, and to add and remove Pepperdata dashboard users.
Prerequisites
- To add a Pepperdata user, you must have group administrator privileges.
Procedure
-
On the dashboard navigation bar, click the gear icon () and select User Management.
-
If the User Management option is missing and you know that you have been granted group administrator privileges, log out of the Pepperdata dashboard and log back in to ensure that your browser cache is refreshed with your group administrator privileges. If the User Management option is still missing, contact Pepperdata Support.
-
If you have group administrator privileges, the Group Admin page appears.
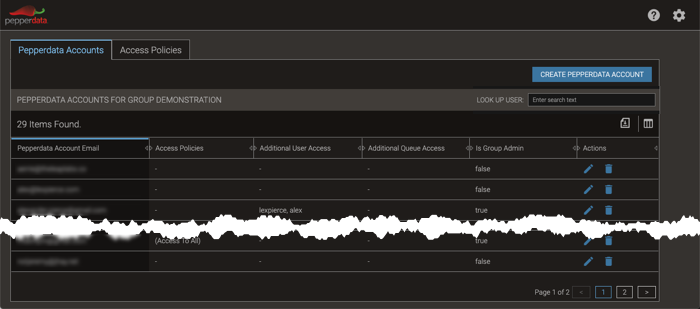
-
-
Click .
-
Step through the Add New Pepperdata Account wizard to configure the new account:
-
Pepperdata Account—The user’s email address—and click Next: Apply Policy.
-
Apply Policy—Optionally select Is Group Admin to grant group administrator privileges (and access to all users and queues) to the new user, and make a policy selection:
-
No policy—Disable access to all users and queues. For such cases, you should apply an inline policy in the next step of the wizard, to configure which users and queues this new user can access.
-
Access to all—Grant access to all users and queues.
-
Apply specific policies—Select one or more access policies for this new user.
-
-
Click Next: Inline Policy (Optional).
-
Inline Policy—Optionally add access for this new user to additional users and queues. For multiple users or queues, enter the names as a comma-separated list.
-
-
Click Save.
The user will receive an email message from Pepperdata with instructions for resetting their password. If they do not see the message within an hour, even after checking their spam folder, contact Pepperdata Support.
Change a Pepperdata User’s Access Permissions (Privileges)
You can change a Pepperdata user’s access permissions (privileges) anytime. For example, you might want to grant administrator permission to another person in order to distribute the administrative workload. Or if someone takes on a lead role, they’ll likely need access to other users and queues.
Prerequisites
- To change a Pepperdata user’s access permissions, you must have group administrator privileges.
Procedure
-
On the dashboard navigation bar, click the gear icon () and select User Management.
-
If the User Management option is missing and you know that you have been granted group administrator privileges, log out of the Pepperdata dashboard and log back in to ensure that your browser cache is refreshed with your group administrator privileges. If the User Management option is still missing, contact Pepperdata Support.
-
If you have group administrator privileges, the Group Admin page appears.
-
-
In the Pepperdata Accounts tab, locate the user.
You can use the Look Up User search box or scroll through the displayed list of users (you might need to use the page controls at the bottom of the table).
-
In the row for the user, click the edit icon (edit).
-
Revise the user’s policy and/or optional inline policy selections, and click Save.
Verify a Pepperdata User’s RBAC Permissions (Privileges)
Anyone (except group administrators, who by definition have access to everything) can verify what their RBAC permissions (privileges) are, which can be very helpful for confirming the result of the access policy/policies that are currently applied. If a user reports that they cannot access resources—see certain things on the Pepperdata dashboard, such as applications or queues—the group administrator should ask the person to view their permissions and send the results (perhaps as a screenshot).
- If the permissions are correct, the group administrator can then explain why certain resources are unavailable.
- If more permissions should be granted, the group administrator can apply different, more, or inline access policies to the applicable user’s account (see Change a Pepperdata User’s Access Permissions).
Procedure
-
On the dashboard navigation bar, click the gear icon () and select My Permissions.
A table showing the user’s permissions appears, similar to this example.
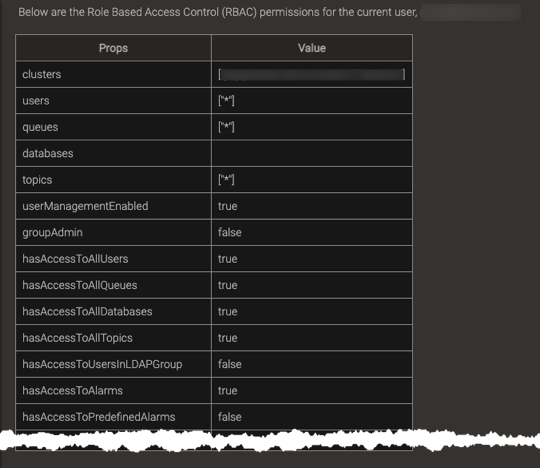
Delete a Pepperdata User
In accordance with security best practices, you should delete users who leave your organization or who no longer need access to the Pepperdata dashboard.
Prerequisites
- To delete a user, you must have group administrator privileges.
Procedure
-
On the dashboard navigation bar, click the gear icon () and select User Management.
-
If the User Management option is missing and you know that you have been granted group administrator privileges, log out of the Pepperdata dashboard and log back in to ensure that your browser cache is refreshed with your group administrator privileges. If the User Management option is still missing, contact Pepperdata Support.
-
If you have group administrator privileges, the Group Admin page appears.
-
-
In the Pepperdata Accounts tab, locate the user.
You can use the Look Up User search box or scroll through the displayed list of users (you might need to use the page controls at the bottom of the table).
-
In the row for the user, click the delete icon (delete), and confirm by clicking Yes.
Warning: You cannot undo this operation. If you remove the wrong user, you can add them back, and they will receive the same email messages as a new user, and will need to change their password again.
About Access Policies
Access policies contain a common set of permissions that can be applied to one or more users.
Resources
Resources that can be granted or restricted include:
-
Clusters—access to all the clusters that were created for your group at Pepperdata-deployment time, or to only specific clusters
-
Cluster users (refers to application users, not Pepperdata dashboard/account users)—no access to any users, access to all users, or access to only specific users
It’s common to want to grant access for many people to a given set of clusters, but to restrict each person’s access to a unique set of cluster users. For this scenario, we recommend setting the Cluster Users access to None, and in each Pepperdata account/user’s settings, to grant access to the required cluster users.
In access policies, the settings for cluster users and queues combine to affect what a Pepperdata user can see (access); see Cluster Users and Queues.
-
Queues—no access to any queues, access to all queues, or access to only specific queues
In access policies, the settings for queues and cluster users combine to affect what a Pepperdata user can see (access); see Combined Privileges for Cluster Uses and Queues.
-
Databases—no access to any databases or access to all databases
-
Topics—no access to any topics, access to all topics, or access to only specific topics
- Alarms—no access to any alarms, access (view and edit) to all alarms, or a custom policy where you can select any/all of the following:
- View and edit Pepperdata-created (predefined) alarms
- View and edit only one’s own alarms
Support for alarms was added after the initial RBAC implementation. To support the original functionality, and not remove access that was previously granted, access was set to all alarms for all access policies that were created before February 23, 2021. -
Custom dashboards—no access to any custom dashboards (including My Dashboard) or access to all custom dashboards
Support for custom dashboards was added after the initial RBAC implementation. To support the original functionality, and not add access that was previously restricted, access was set to no custom dashboards for for all access policies that were created before May 11, 2021. -
Analysis Reports—no access to any reports, access to all reports, or access to only specific reports.
Support for Analysis Reports was added after the initial RBAC implementation. To support the original functionality, and not add access that was previously restricted, access was set to no reports for all access policies that were created before August 26, 2021. Group administrators retain access to all Analysis Reports.
Combined Privileges for Cluster Users and Queues
The table shows how the combination of access settings for cluster users and queues affects which apps a Pepperdata user can see (has access to see) in the dashboard. Similarly, which cluster users and queues a user can access affects which charts are shown in custom dashboards and My Dashboard.
| Cluster Users Setting | Queues Setting | Pepperdata User Sees... |
| None | None | No apps (because no access to any cluster users) |
| All Queues | ||
Custom: queue-one |
||
| All Users | None | No apps (because no access to any queues) |
| All Queues | All apps (because access is granted to all users and all queues) | |
Custom: queue-one |
Apps run in the queue-one queue (by all users) |
|
Custom: bob |
None | No apps (because no access to any queues) |
| All Queues | All apps run by cluster user bob (in any queue) |
|
Custom: queue-one |
Apps run by bob in the queue-one queue |
Restricted Users
Restricted users are Pepperdata users who have access to only a subset of resources, as defined by the access policy/policies that are applied to their account. The dashboard pages show only the resources that such users are permitted to access. For example, the Applications Overview (the default “home” page for restricted users) table shows the subset of applications that the user has permission to access, but none of the other applications in the cluster, even if the would otherwise be a match for the selected filters (such as time range).
The table shows how the content of the Pepperdata dashboard display changes based on whether or not a user is a restricted user.
| Function/View | Restricted User Sees/Can Do... | Unrestricted User Sees/Can Do... |
| Dashboard landing page | Applications Overview, filtered to apps run by accessible cluster users on accessible queues | Pepperdata Dashboard (the Home page that shows tiles for Cluster Resources, Queues, Recommendations, and so on) |
| Application Spotlight: Applications, Workflows | Overviews and Details pages filtered to apps/workflows run by accessible cluster users on accessible queues | Overviews and Details pages that show all apps and workflows |
| Platform Spotlight: All Overviews | Overviews filtered to show only resources associated with accessible cluster users and queues | Overviews that show all resources in the cluster |
| Query Spotlight: Queries, Databases |
|
Overviews and Details pages for all queries and databases |
| Capacity Optimizer Overview |
|
Can view the page |
| Application Profiler, Query Profiler, and Recommendations | Profiler information and Recommendations (in applicable Details tabs) for accessible applications and queries | Profiler information and Recommendations for all applications and queries in the cluster |
| Streaming Spotlight: Brokers, Topics |
|
Overview and Details pages for all brokers and topics |
| Reports | Not available | All reports |
| Custom Dashboards | Accessible custom dashboards | All custom dashboards |
| My Dashboard | Charts filtered to show only resources associated with dashboard-configured (personalized) and accessible cluster users and queues | Charts that show all dashboard-configured (personalized) resources in the cluster |
| Dashboard Configuration: Cost values for usage/Chargeback reporting, Display settings (the cost in either currency or resources/hour), Slack Config |
|
Can configure/change values |
| Pepperdata REST APIs | Can access the same resources that are permitted through the dashboard UI (user interface) | Can access all resources |
Add an Access Policy
Prerequisites
- To add an access policy, you must have group administrator privileges.
Procedure
-
On the dashboard navigation bar, click the gear icon () and select User Management.
-
If the User Management option is missing and you know that you have been granted group administrator privileges, log out of the Pepperdata dashboard and log back in to ensure that your browser cache is refreshed with your group administrator privileges. If the User Management option is still missing, contact Pepperdata Support.
-
If you have group administrator privileges, the Group Admin page appears.
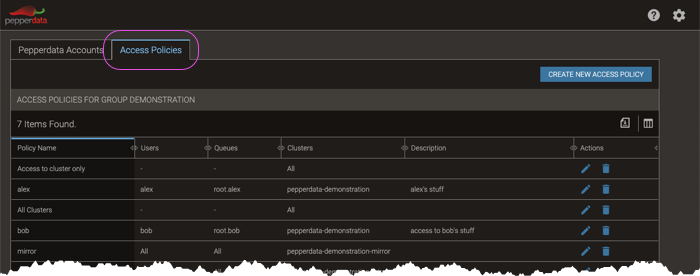
-
-
Select the Access Policies tab, and click .
-
Step through the Create Access Policy wizard to configure the new access policy:
-
Enter the Policy Name and optionally a description, and click Next: Clusters.
-
Select the Clusters to include in this policy, and click Next: Cluster Users.
-
Select the Cluster Users to include in this policy (for multiple, specific users, enter the names as a comma-separated list), and click Next: Queues.
-
Select the Queues to include in this policy (for multiple, specific queues, enter the names as a comma-separated list), and click Next: Databases.
-
Select the Databases to include in this policy, and click Next: Topics.
-
Select the Topics to include in this policy (for multiple, specific topics, enter the names as a comma-separated list), and click Next: Alarms.
-
Select the Alarms to include in this policy.
With the Custom option, you can select any combination of the following:
- View and edit Pepperdata predefined alarms
- Create, view, and edit own alarms
- (If applicable) View and edit all alarms of all users in own LDAP group
- Limit the number of alarms this user can create per realm
Make your selection(s)—None, All Alarms, or any combination of Custom options—and click Next: Custom Dashboards.
-
Select the Custom Dashboards to include in this policy.
With the Custom option, you can select any combination of the following:
- Create, view, and edit own custom dashboards
- (If applicable) View and edit all shared custom dashboards of all users in own LDAP group
- Limit the number of dashboards this user can create per realm
Make your selection(s)—None, All Dashboards, or any combination of Custom options—and click Next: Analysis Reports.
-
Select the Analysis Reports to include in this policy. With the Custom option, you can select any combination of reports.
Make your selection(s)—None, All, or any combination of Custom options.
-
-
Click Save.
Change (Edit) an Access Policy
You can change (edit) an access policy anytime.
For example, if another development cluster is added, dev-12, you’d likely want to add it to the Clusters section of an access policy named Dev Clusters.
Or if a queue is reassigned to a different team, you’d likely want to move that queue from one team’s access policy to the policy for the team that now has that queue.
Prerequisites
- To change an access policy, you must have group administrator privileges.
Procedure
-
On the dashboard navigation bar, click the gear icon () and select User Management.
-
If the User Management option is missing and you know that you have been granted group administrator privileges, log out of the Pepperdata dashboard and log back in to ensure that your browser cache is refreshed with your group administrator privileges. If the User Management option is still missing, contact Pepperdata Support.
-
If you have group administrator privileges, the Group Admin page appears.
-
-
Select the Access Policies tab, and locate the access policy that you want to change.
-
In the row for the access policy, click the edit icon (edit).
-
Revise any of the policy elements that you want, and click Save.
Delete an Access Policy
You can delete access policies anytime. For example, you might have configured a policy for access to test equipment that is then moved to production, so the “test” policy is no longer needed.
Prerequisites
- To delete an access policy, you must have group administrator privileges.
Procedure
-
On the dashboard navigation bar, click the gear icon () and select User Management.
-
If the User Management option is missing and you know that you have been granted group administrator privileges, log out of the Pepperdata dashboard and log back in to ensure that your browser cache is refreshed with your group administrator privileges. If the User Management option is still missing, contact Pepperdata Support.
-
If you have group administrator privileges, the Group Admin page appears.
-
-
Select the Access Policies tab, and locate the access policy that you want to delete.
-
In the row for the access policy, click the delete icon (delete), and confirm by clicking Yes.
