Configure Encryption (Parcel)
In addition to the transport-level encryption that is always in effect between your cluster and Pepperdata, and the secure https access that the Pepperdata dashboard requires, you can enable 128-bit AES-CBC (symmetric) storage-level encryption for sensitive data at rest, such as user names, hostnames, and job and queue names.
When this extra level of encryption is enabled, Pepperdata receives and stores only the encrypted version.
To configure encryption for your cluster, add the PD_ENCRYPTION_KEY and PD_ANONYMIZE variables to your Pepperdata configuration.
Notes and Limitations
-
When you enable encryption, the dashboard by default shows the data in its encrypted form. To view the decrypted data, you must enter the encryption key (which is also used to decrypt the data) into any dashboard page.
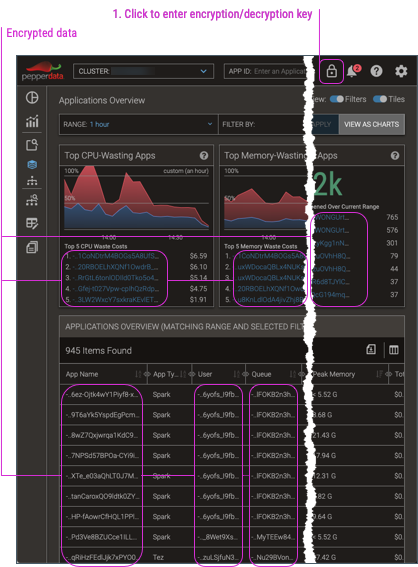
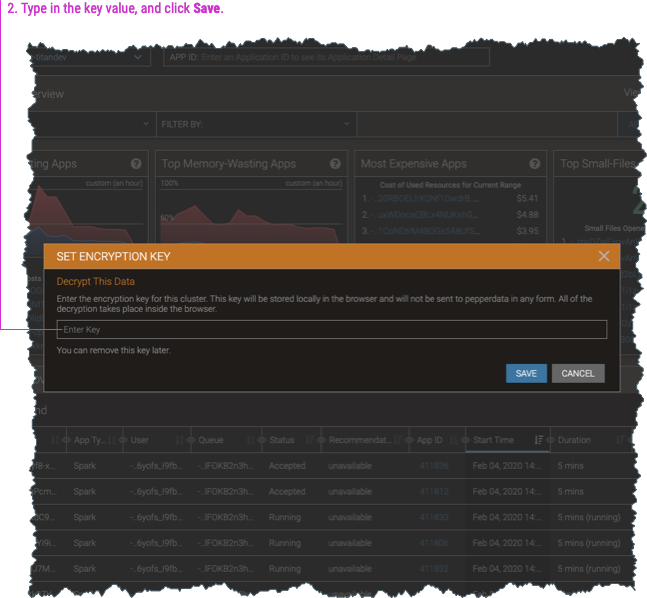
-
Impala data cannot be encrypted.
-
Although you can perform full-text searches for application names even with encryption, partial matches are unsupported. For example, if the application name is “hive”, searching for “hive” yields the expected result. But when encryption is applied to perform the search, the encrypted value for a partial search string will not match any portion of the encrypted value of the full string. Therefore “hiv” cannot be matched if the full name of the application is “hive”.
-
If you use the Pepperdata REST API to access data from encrypted clusters, you’ll need to decrypt the returned data strings; see Decrypt Data Returned for Encrypted Clusters.
Procedure
-
Generate an encryption key, which is also used to decrypt the data for your Pepperdata dashboard display.
-
You can use a commercial or open source tool to create a randomly-generated key; for example, the OpenSSL command,
openssl rand -hex 16. -
You can manually create any arbitrary string to use as your key; for example,
MyCustomEncryptionKey. -
Be sure to keep your key secret and secure in accordance with your organization’s security policies.
-
-
Use Cloudera Manager to add the required environment variables to the Pepperdata > Configuration > PepCollector > PepCollector Environment Advanced Configuration Snippet (Safety Valve) template.
Be sure to replace the
my-encrypt-decrypt-keyplaceholder with your actual encryption key.PD_ENCRYPTION_KEY=my-encrypt-decrypt-key PD_ANONYMIZE=1 -
In Cloudera Manager, select the Restart action for the PepCollector service.
